Demystifying HIPAA Compliance: Key Insights for Healthcare Providers
Navigating and implementing HIPAA compliance for healthcare providers can be complex, overwhelming, and demanding at the same time. However, it’s essential for anyone with access to patient information to understand and comply with this vital legal and ethical framework. SAAS solutions like AffableBPM offer a secure document repository, granting authorized users access to the information relevant to their roles. To address common misconceptions and questions, we’ve created this article to provide a clear and concise guide to HIPAA standards and provisions.
HIPAA Simplified: Essential Points
In a nutshell, HIPAA, which stands for Health Insurance Portability and Accountability Act, was enacted in 1996 to modernize healthcare information flow and protect patient medical data. Here are the key aspects of HIPAA:
- Facilitates seamless health insurance coverage transfer for individuals changing or losing jobs in the USA.
- Combats healthcare fraud and abuse.
- Mandates secure electronic access to billing, claims, referrals, and other processes for healthcare organizations.
- Sets standards for the transmission and handling of patient information.
HIPAA comprises five titles:[1]
- Health Care Access, Portability, and Renewability: Regulates health insurance coverage availability for workers and their families during job transitions.
- Administrative Simplification: Provisions, establishes national standards for electronic health care transactions and all covered entities to ensure privacy and security of individually identifiable health information.
- Tax Related Health Provisions: Provides guidelines for pre-tax medical spending accounts.
- Application & Enforcement of Group Health Plan Requirements: Outlines rules for group health plans.
- Revenue Offsets: governs company-owned life insurance policies.
In essence, HIPAA safeguards patient information, preventing misuse, theft, or embezzlement of personal healthcare data.
What is a Covered Entity?
“Covered entities are defined in the HIPAA rules as (1) health plans, (2) health care clearinghouses, and (3) health care providers who electronically transmit any health information in connection with transactions for which HHS (Health and Human Services) has adopted standards. Generally, these transactions concern billing and payment for services or insurance coverage.” [2]
What is a Business Associate?
A “business associate” refers to an individual or organization that performs specific functions or activities involving the use or disclosure of Protected Health Information (PHI) on behalf of a covered entity. [3] Examples of business associates include lawyers, accountants, IT contractors, billing companies, cloud storage services, and email encryption services, among others. Before accessing PHI, a business associate must sign a Business Associate Agreement with the covered entity. This agreement outlines the specific PHI they can access, how it should be used, and the requirement to return or destroy the information once the task is completed. While in possession of PHI, the business associate shares the same HIPAA compliance obligations as a covered entity.
Understanding HIPAA Compliance
4 Key HIPAA Compliance Guidelines for Healthcare Providers are as follows:
- Privacy Rules
- Security Rules
- Breach Notification Rules
- Enforcement Rules
Privacy Rules
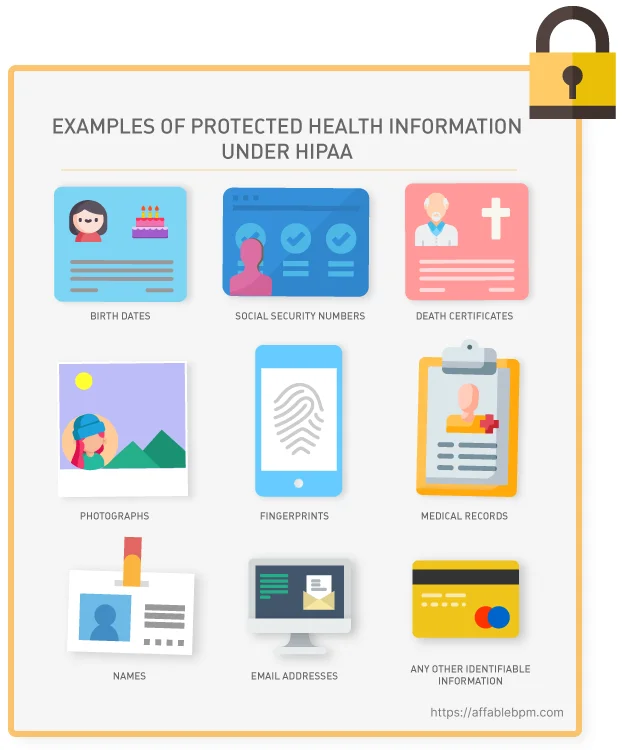
Under HIPAA privacy rules, healthcare providers are obligated to grant individuals access to their Protected Health Information (PHI), which encompasses health conditions, treatment plans, notes, images, lab results, and billing details. The privacy rule outlines the permissible uses and disclosures of PHI by healthcare professionals, lawyers, and other authorized entities. It applies to all forms of PHI, whether stored or transmitted electronically, on paper, or through oral communication by a covered entity or its business associates.
Security Rules
The HIPAA Security Rule works hand-in-hand with the Privacy Rule to establish the necessary national standards for covered entities in handling electronic Protected Health Information (ePHI). This rule focuses on safeguarding ePHI through various measures. “The Security Rule requires appropriate administrative, physical and technical safeguards to ensure the confidentiality, integrity, and security of ePHI.” [4]
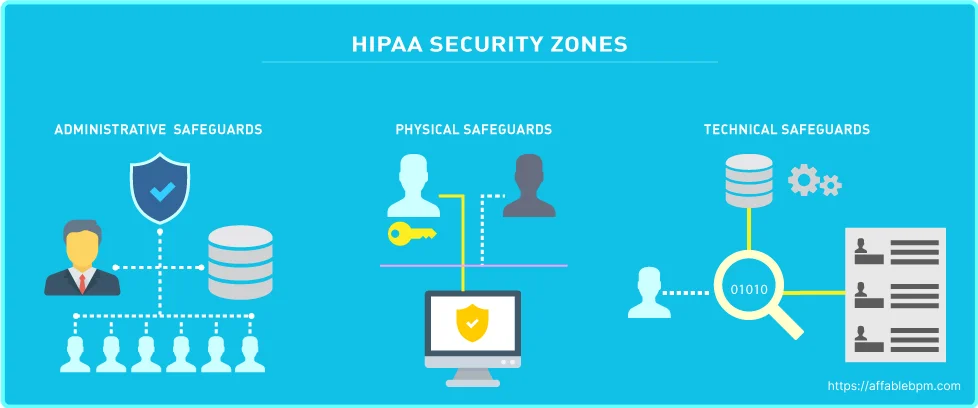
The HIPAA Security Rule consists of three categories with specific standards, which are detailed below: [5]
- Technical Safeguards: Technical safeguards focus on the technology used to protect ePHI within covered entities. It is crucial for covered entities to comply with the Technical Safeguard standards and implementation specifications outlined in the Security Rule. Following are the Key Standards:
- Access Controls: Providing unique user identification, emergency access procedures, automated session termination, and encryption/decryption methods for ePHI storage are some of the important considerations to ensure proper access control to ePHI.
- Audit Controls: Regular assessment, recording, and storage of system usage and ePHI handling through audit reports or similar mechanisms are a must to determine occurrence of a security violation.
- Integrity Controls: Implementing policies and procedures from both technical and non-technical compromise is necessary to protect ePHI. A periodic risk analysis and mitigation measures are required to be conducted on a regular basis by covered entities.
- Person or Entity Authentication: Establishing authentication measures (e.g., passwords, smart cards, biometric safeguards) to ensure authorized access to information and ePHI is a must.
- Transmission Security: Allows ePHI to be transmitted over protected electronic open networks, using implementation specifications such as integrity controls and/or encryption mechanism. [6]
- Physical Safeguards: The Physical Safeguards address the physical access to ePHI regardless of its storage location, whether it’s a remote data center, cloud environment, or on-site servers of the HIPAA covered entity. These safeguards also provide guidelines on securing workstations and mobile devices to prevent unauthorized access. [7] The following are the key standards as part of Physical Safeguards.
- Facility Access Controls: Policies and procedures must be in place to restrict physical access to electronic information systems and the facilities where they are housed. These measures ensure that only authorized personnel are granted access while maintaining the necessary security protocols.
- Workstation Use: Lists policies and procedures that define the specific functions to be performed, the appropriate manner of performing those functions, and the physical attributes of the workstation environment. A workstation is defined in the rule as “an electronic computing device, for example, a laptop or desktop computer, or any other device that performs similar functions, and electronic media stored in its immediate environment.” [7]
- Workstation Security: Workstation Security entails implementing physical safeguards for all workstations that access ePHI to prevent unauthorized access. It complements the Workstation Use standard, by specifically focusing on securing workstations from unauthorized users through physical measures.
- Device and Media Controls: The Device and Media Controls standard mandates the establishment of policies and procedures to manage the receipt, removal, and movement of hardware and electronic media containing ePHI. This includes controlling the entry and exit of such items from a facility, as well as their internal movement within the facility. The goal is to ensure proper safeguards and control measures are in place to protect the confidentiality, integrity, and security of ePHI stored on devices and media.
- Administrative Safeguards: The Administrative Safeguards encompass the policies and procedures that bridge the Privacy Rule and the Security Rule. These safeguards mandate the appointment of a Security Officer and a Privacy Officer who are responsible for implementing measures to protect ePHI. They also have the responsibility of overseeing the workforce’s adherence to privacy and security guidelines. Following are the Key Standards [8]
- Security Management Process: This Process mandates that covered entities establish policies and procedures to prevent, detect, contain, and correct security violations. It consists of four specific implementation specifications:
- Risk Analysis: Conducting a thorough assessment of potential risks and vulnerabilities to the confidentiality, integrity, and availability of ePHI.
- Risk Management: Implementing measures to mitigate identified risks and vulnerabilities, ensuring the ongoing protection of ePHI.
- Sanction Policy: Enforcing appropriate sanctions against workforce members who violate the security policies and procedures of the covered entity.
- Information System Activity Review: Regularly reviewing information system activity through activities such as auditing logs, access reports, and tracking security incidents.
- Assigned Security Responsibility: It is crucial to designate a security official who is responsible for consistently reviewing, developing, and maintaining privacy policies and strategies. This individual plays a vital role in ensuring compliance with privacy guidelines.
- Workforce Security: To maintain appropriate access controls and prevent unauthorized access to ePHI, it is essential to ensure that only authorized individuals have the necessary access privileges while preventing unauthorized personnel from obtaining access to ePHI.[9]
- Security Awareness and Training: Security awareness and training play a critical role in ensuring the effectiveness of safeguards, given that many security risks and vulnerabilities originate internally. Covered entities are required to establish a comprehensive security awareness and training program for all workforce members, including management.
- Evaluation System: To ensure the ongoing effectiveness of security plans and procedures in protecting ePHI, it is crucial for a covered entity to assess employees’ adherence to ePHI handling practices and identify areas for improvement. Regular monitoring and evaluation of policies and procedures help maintain compliance and proactively address any potential vulnerabilities or gaps in security measures.[9]
- Security Management Process: This Process mandates that covered entities establish policies and procedures to prevent, detect, contain, and correct security violations. It consists of four specific implementation specifications:

Breach Notification Rule
Under the HIPAA Breach Notification Rule, covered entities are obligated to inform individuals within 60 days if there has been unauthorized access to their PHI. It’s important to note that even if ePHI is encrypted by ransomware, it is still considered a breach and falls under this rule. If the breach affects more than 500 PHI records, the covered entity must notify the Department of Health and Human Services, which may involve the Office for Civil Rights (OCR). Additionally, in such cases, the covered entity is required to issue a press release about the breach to inform the public. [10]
Enforcement Rule
The Enforcement Rule outlines the compliance responsibilities of covered entities in terms of cooperation during the enforcement process. When individuals or organizations report HIPAA violations to the Office for Civil Rights (OCR), the OCR is responsible for investigating and reviewing those reported violations. The Enforcement Rule sets forth guidelines for determining the amount of civil penalties in case of a violation and establishes procedures for hearings and appeals if a covered entity contests a violation determination. It ensures a fair and structured enforcement process for addressing HIPAA violations and resolving disputes.
Covered entities should be aware of the following penalties as per the violation tier:[12]
- Tier 1: A violation attributable to ignorance can attract a fine of $127 – $31,98750,000.
- Tier 2: A violation which occurred despite reasonable vigilance can attract a fine of $1,280 – $563,973.
- Tier 3: A violation due to willful neglect which is corrected within thirty days will attract a fine of between $12,794 and $63,973.
- Tier 4: A violation due to willful neglect which is not corrected within thirty days will attract the minimum fine of $63,973.
Fines for HIPAA violations are assessed based on various factors, including the category of violation, the number of records exposed in a breach, the level of risk associated with the data exposure, and the degree of negligence demonstrated. The maximum fine per year for the most serious Tier 4 violation can reach up to $1,919,173. In cases of willful neglect, criminal charges can also be filed. Additionally, victims of a breach have the option to pursue civil lawsuits to seek damages. The entities most commonly subject to enforcement include private medical practices, hospitals, outpatient facilities such as pain clinics or rehabilitation centers, insurance groups, and pharmacies. It is crucial for these organizations to prioritize HIPAA compliance to mitigate the risk of penalties and legal consequences.
Understanding HIPAA Violation
HIPAA requirements can be violated in various ways, with the most common being negligence or incomplete compliance, leading to data breaches, unauthorized release ofPHI, or access by unauthorized employees. HIPAA violations can persist for extended periods, often going unnoticed for months or even years. The penalties for such violations increase as their duration extends. Therefore, it is crucial for HIPAA-covered entities to conduct regular compliance reviews to proactively identify and address any potential violations before they are discovered by regulatory authorities.
There are three main ways that HIPAA violations are discovered: [11]
- Investigations into a data breach by OCR (or state attorneys general)
- Investigations into complaints about covered entities and business associates
- HIPAA compliance audits
Even in cases where a data breach does not directly involve a HIPAA violation or a complaint is found to be unfounded, the Office for Civil Rights (OCR) may still uncover unrelated HIPAA violations during their investigations. If such violations are discovered and deemed significant, they may lead to the imposition of financial penalties or other enforcement actions. [11]
HIPAA Risk Assessment
Within the HIPAA regulations, there is a notable absence of specific guidance on the content and components of a HIPAA risk assessment. However, the Department of Health and Human Services emphasizes that the purpose of a HIPAA risk assessment is for a Business Associate to proactively evaluate their organization internally and identify potential vulnerabilities, threats, and risks related to PHI they handle. While the exact approach may vary depending on the organization, here are some common objectives of a HIPAA risk assessment:
- Identify PHI: One of the objectives of a HIPAA risk assessment is to identify the PHI that your organization creates, receives, stores, and transmits. This includes not only the PHI handled internally but also the PHI shared with consultants, vendors, and business associates.
- Identify Potential Vulnerabilities: Assess the systems, processes, and infrastructure within the organization to identify any potential weaknesses or vulnerabilities that could compromise the security or privacy of PHI.
- Evaluate Threats: Determine the various internal and external threats that could potentially lead to unauthorized access, disclosure, or loss of PHI. This includes considering factors such as cyber threats, physical security risks, and human factors.
- Assess Risks: Analyze the likelihood and impact of identified threats to PHI, taking into account the potential harm to individuals, legal and financial consequences, and the organization’s reputation.
- Mitigation Strategies: Develop and implement strategies and controls to mitigate identified risks and vulnerabilities. This may involve implementing technical safeguards, security policies and procedures, training programs, and incident response plans.
- Documentation and Compliance: Maintain thorough documentation of the risk assessment process, findings, and actions taken to address identified risks. Ensure ongoing compliance with HIPAA regulations and regularly review and update risk assessments as needed.
“The HIPAA risk assessment, the rationale for the measures, procedures, and policies subsequently implemented, and all policy documents must be retained for a minimum of six years.” [12]
HIPAA compliance is about fostering trust with customers by safeguarding their data. Compliance with HIPAA is an ongoing commitment, requiring continuous efforts rather than a one-time assessment. It is essential for Covered Entities and Business Associates to remain vigilant in their understanding and implementation of HIPAA requirements. Healthcare solution such as AffableBPM, based on HIPAA compliant Microsoft Azure services, make contractual assurances about data safeguarding, reporting including breach notifications and data access in accordance with HIPAA. [13] Seeking professional advice is highly recommended if any aspect of HIPAA raises concerns or uncertainties. Ignorance of HIPAA does not serve as an excuse for noncompliance, and the responsibility to comprehend, adopt, and maintain HIPAA guidelines is significant. Prioritizing compliance is crucial for the long-term success and reputation of organizations handling PHI.
References >
[1] https://privacyruleandresearch.nih.gov/pr_06.asp
[2] https://www.hhs.gov/hipaa/for-professionals/privacy
[3] https://www.hhs.gov/hipaa/for-professionals/security
[4] https://www.hhs.gov/hipaa/for-professionals/security
[8] https://www.hipaajournal.com/hipaa-compliance-check
[9] https://www.hhs.gov/hipaa/for-professionals/breach
[10] https://www.hipaajournal.com/common-hipaa-violations
Navigating and implementing HIPAA can be complex, overwhelming, and demanding at the same time. However, it’s essential for anyone with access to patient information to understand and comply with this vital legal and ethical framework. SAAS solutions like AffableBPM offer a secure document repository, granting authorized users access to the information relevant to their roles. Leveraging Artificial Intelligence in Healthcare, and advanced Healthcare Automation Solutions ensures secure, efficient data management. To address common misconceptions and questions, we’ve created this article to provide a clear and concise guide to HIPAA standards and provisions.
HIPAA Simplified: Essential Points
In a nutshell, HIPAA, which stands for Health Insurance Portability and Accountability Act, was enacted in 1996 to modernize healthcare information flow and protect patient medical data. Here are the key aspects of HIPAA:
- Facilitates seamless health insurance coverage transfer for individuals changing or losing jobs in the USA.
- Combats healthcare fraud and abuse.
- Mandates secure electronic access to billing, claims, referrals, and other processes for healthcare organizations.
- Sets standards for the transmission and handling of patient information.
HIPAA comprises five titles[1]:
- Health Care Access, Portability, and Renewability: Regulates health insurance coverage availability for workers and their families during job transitions.
- Administrative Simplification: Provisions, establishes national standards for electronic health care transactions and all covered entities to ensure privacy and security of individually identifiable health information.
- Tax Related Health Provisions: Provides guidelines for pre-tax medical spending accounts.
- Application & Enforcement of Group Health Plan Requirements: Outlines rules for group health plans.
- Revenue Offsets: governs company-owned life insurance policies.
In essence, HIPAA safeguards patient information, preventing misuse, theft, or embezzlement of personal healthcare data.
What is a Covered Entity?
“Covered entities are defined in the HIPAA rules as (1) health plans, (2) health care clearinghouses, and (3) health care providers who electronically transmit any health information in connection with transactions for which HHS (Health and Human Services) has adopted standards. Generally, these transactions concern billing and payment for services or insurance coverage.” [2]
What is a Business Associate?
A “business associate” refers to an individual or organization that performs specific functions or activities involving the use or disclosure of Protected Health Information (PHI) on behalf of a covered entity. [3] Examples of business associates include lawyers, accountants, IT contractors, billing companies, cloud storage services, and email encryption services, among others. Before accessing PHI, a business associate must sign a Business Associate Agreement with the covered entity. This agreement outlines the specific PHI they can access, how it should be used, and the requirement to return or destroy the information once the task is completed. While in possession of PHI, the business associate shares the same HIPAA compliance obligations as a covered entity.
Understanding HIPAA Compliance
4 Key HIPAA Compliance Guidelines for Healthcare Providers are as follows:
- Privacy Rules
- Security Rules
- Breach Notification Rules
- Enforcement Rules
Privacy Rules
Consistent with HIPAA privacy regulations, professionals in the field of healthcare have duties to provide access to the protected health information (PHI) of individuals, including their health history, service-agency records, notes, images, laboratory findings, and billing data. The rule covers assured allowable uses and disclosures of PHI by various healthcare professionals, attorneys, and other covered entities. It applies to all forms of PHI, whether stored or transmitted electronically, on paper, or through oral communication by a covered entity or its business associates.

Security Rules
The HIPAA Security Rule, which works hand-in-hand with the Privacy Rule, establishes the required national standards for covered entities to conduct their business involving the electronic Protected Health Information (ePHI). This rule specifically concentrates on the various protections guaranteed to ePHI. “The Security Rule requires appropriate administrative, physical and technical safeguards to ensure the confidentiality, integrity, and security of ePHI.”[4]

The HIPAA Security Rule consists of three categories with specific standards, which are detailed below [5]:
- Technical Safeguards: Technical safeguards focus on the technology used to protect ePHI within covered entities. It is crucial for covered entities to comply with the Technical Safeguard standards and implementation specifications outlined in the Security Rule. Following are the Key Standards:
- Access Controls: Providing unique user identification, emergency access procedures, automated session termination, and encryption/decryption methods for ePHI storage are some of the important considerations to ensure proper access control to ePHI.
- Audit Controls: Regular assessment, recording, and storage of system usage and ePHI handling through audit reports or similar mechanisms are a must to determine occurrence of a security violation.
- Integrity Controls: Implementing policies and procedures from both technical and non-technical compromise is necessary to protect ePHI. A periodic risk analysis and mitigation measures are required to be conducted on a regular basis by covered entities.
- Person or Entity Authentication: Establishing authentication measures (e.g., passwords, smart cards, biometric safeguards) to ensure authorized access to information and ePHI is a must.
- Transmission Security: Allows ePHI to be transmitted over protected electronic open networks, using implementation specifications such as integrity controls and/or encryption mechanism.[6]
- Physical Safeguards: The Physical Safeguards address the physical access to ePHI regardless of its storage location, whether it’s a remote data center, cloud environment, or on-site servers of the HIPAA covered entity. These safeguards also provide guidelines on securing workstations and mobile devices to prevent unauthorized access.[7] The following are the key standards as part of Physical Safeguards.
- Facility Access Controls: However, in order for any organization to physically restrict access to electronic information systems and facilities where they are housed, policies and procedures must be in place. Only authorized personnel will have access, while the security protocols are maintained.
- Workstation Use: Lists policies and procedures that define the specific functions to be performed, the appropriate manner of performing those functions, and the physical attributes of the workstation environment. A workstation is defined in the rule as “an electronic computing device, for example, a laptop or desktop computer, or any other device that performs similar functions, and electronic media stored in its immediate environment.”[7]
- Workstation Security: Workstation Security requires physical safeguards for all workstations accessing ePHI in an effort to prevent unauthorized access to them. In a complementary manner, the Workstation Use standard focuses on specific safeguards to set up when it comes to the protection of workstations against being accessed by unauthorized users using physical measures.
- Device and Media Controls: The Device and Media Controls standard directs policies and procedures for the receipt, removal, and movement of hardware and electronic media that store ePHI. This is done by controlling its entry and exit from a facility and controlling its internal movements within a facility. The purpose is to establish adequate protections and controls to assure the confidentiality, integrity, and security of ePHI on devices and media.
- Administrative Safeguards: The Administrative Safeguards are made up of policies and procedures(s) that interconnect the Privacy Rule and the Security Rule. The safeguards would, for instance, require that a Security Officer and a Privacy Officer be appointed to ensure protection of ePHI. They would also inspect the extent to which the workforce adheres to privacy and security guidelines. Following are the Key Standards [8]
- Security Management Process: This Process mandates that covered entities establish policies and procedures to prevent, detect, contain, and correct security violations. It consists of four specific implementation specifications:
- Risk Analysis: Conducting a thorough assessment of potential risks and vulnerabilities to the confidentiality, integrity, and availability of ePHI.
- Risk Management: Implementing measures to mitigate identified risks and vulnerabilities, ensuring the ongoing protection of ePHI.
- Sanction Policy: Enforcing appropriate sanctions against workforce members who violate the security policies and procedures of the covered entity.
- Information System Activity Review: Regularly reviewing information system activity through activities such as auditing logs, access reports, and tracking security incidents.
- Assigned Security Responsibility: A security official should be named to always express satisfaction, develop and maintain privacy policies and strategies as one of the key people who will implement compliance with the privacy policy.
- Workforce Security: For access control, it is necessary to create a distinction that allows only authorized personnel to access ePHI without also allowing unauthorized personnel to access this sensitive but protected data. [9]
- Security Awareness and Training: Security awareness and training play a critical role in ensuring the effectiveness of safeguards, given that many security risks and vulnerabilities originate internally. Covered entities are required to establish a comprehensive security awareness and training program for all workforce members, including management.
- Evaluation System: Security awareness and training play a crucial role in ensuring that the safeguards would be effective since many security threats and vulnerabilities arise from within. Covered entities shall have a comprehensive security awareness and training program for all the workforce members, including management.[9]

Breach Notification Rule
Under the HIPAA Breach Notification Rule, any Covered Entity must notify individuals within 60 days of any unauthorized access to protected health information. These considerations state that even if ePHI is encrypted by ransomware, it still is a breach and looks as such under this rule. If the breach affects more than 500 records of PHI, the Covered Entity shall notify the Department of Health and Human Services, which may involve the Office for Civil Rights (OCR). Additionally, in such cases, the covered entity is required to issue a press release about the breach to inform the public. [10]
Enforcement Rule
The Enforcement Rule makes clear the responsibility of covered entities in complying with the cooperation during the enforcement process. Thus authorized by the law, the OCR is to receive complaints regarding a HIPAA violation and to investigate, review, and act upon those complaints. The Enforcement Rule also provides guidance on what civil monetary penalties will be established in the event violations occur and explains what hearings and appeals procedures are to be established if a covered entity challenges a violation finding. It guarantees fairness and structure during the enforcement process addressing HIPAA violations and their related disputes.
Covered entities should be aware of the following penalties as per the violation tier [12]:
- Tier 1: A violation attributable to ignorance can attract a fine of $127 – $31,98750,000.
- Tier 2: A violation which occurred despite reasonable vigilance can attract a fine of $1,280 – $563,973.
- Tier 3: A violation due to willful neglect which is corrected within thirty days will attract a fine of between $12,794 and $63,973.
- Tier 4: A violation due to willful neglect which is not corrected within thirty days will attract the minimum fine of $63,973.
Several factors are considered when determining fines for HIPAA violations, including the specific kind of violation, the amount of protected health information that has been affected by a breach, the level of compromise of the data, and the degree of negligence involved. Peace incidents of these grave Tier 4 violations a fine of as much as $ 1,919,173 may be levied in a year. In some instances of willful neglect, there will also be a criminal charge against the guilty party. Victims from a breach can also undertake a civil suit for redress or damages. Usually, the ones that bear the brunt of these regulations are private practices, hospitals, outpatient facilities such as pain clinics or rehabilitation centers, insurance groups, and pharmacies. It is quite important for these bodies to prepare to comply with HIPAA requirements so that they can avert penalties and the legal consequences that often follow.
Understanding HIPAA Violation
HIPAA regulations can be violated in several ways, the most common being negligence or a passive lapse that has resulted in breaches, unauthorized pairing, or access by unauthorized employees. HIPAA violations may continuously occur over months or even years without anyone knowing. The penalties imposed increase with time. It is therefore important for entities subject to HIPAA to implement regular compliance reviews to detect, reply to, and correct potential violations before such violations are discovered by regulators.
There are three main ways that HIPAA violations are discovered [11]:
- Investigations into a data breach by OCR (or state attorneys general)
- Investigations into complaints about covered entities and business associates
- HIPAA compliance audits
Although, even though a data breach may not directly lead to a HIPAA violation or, in fact, may be found to be without merit by the OCR investigators, the investigators can identify independent HIPAA violation during the investigation. If such violations are detected and deemed serious, they may lead to financial penalties or other actions by enforcement.[11]
HIPAA Risk Assessment
Within the HIPAA regulations, there is a notable absence of specific guidance on the content and components of a HIPAA risk assessment. However, the Department of Health and Human Services emphasizes that the purpose of a HIPAA risk assessment is for a Business Associate to proactively evaluate their organization internally and identify potential vulnerabilities, threats, and risks related to PHI they handle. While the exact approach may vary depending on the organization, here are some common objectives of a HIPAA risk assessment:
- Identify PHI: A goal of a HIPAA risk assessment is to identify what kind of PHI your organization generates, receives, holds and shares. This also encompasses, not just the PHI processed in your organisation but also the PHI shared with consultants, vendors and business associates.
- Identify Potential Vulnerabilities: Analyse the business’s systems, processes, and technology for any security loopholes or vulnerabilities that could jeopardize the security or privacy of PHI.
- Evaluate Threats: Describe all possible threats, both from outside and inside, that could cause disclosure, theft or destruction of PHI. These threats arise from malware, flaws in the design of cyber security application software, and the human one.
- Assess Risks: Assess the probability and consequences of emerging threats to Protected Health Information (PHI). Think of the potential damage to individuals, the legal and financial consequences, and the impact on the organization’s standing.
- Mitigation Strategies: Implementing schemes and preventative measures that will effectively reduce both the acknowledged risks and vulnerabilities. It seems like it may include applying technical safeguards, security policies and procedures, organizing training programs, and incident response plans.
- Documentation and Compliance: Maintain thorough documentation of the risk assessment process, findings, and actions taken to address identified risks. Ensure ongoing compliance with HIPAA regulations and regularly review and update risk assessments as needed.
“The HIPAA risk assessment, the rationale for the measures, procedures, and policies subsequently implemented, and all policy documents must be retained for a minimum of six years.”[12]
HIPAA compliance focuses on building trust with customers by protecting their data. It is an on-going commitment that demands continuous effort, not just a one-time evaluation. Covered Entities and Business Associates must stay alert in their understanding and application of HIPAA requirements. Healthcare Automation solution such as AffableBPM, based on HIPAA compliant Microsoft Azure services, make contractual assurances about data safeguarding, reporting including breach notifications and data access in accordance with HIPAA. [13] Seeking professional advice is highly recommended if any aspect of HIPAA raises concerns or uncertainties. Ignorance of HIPAA does not serve as an excuse for noncompliance, and the responsibility to comprehend, adopt, and maintain HIPAA guidelines is significant. Prioritizing compliance is crucial for the long-term success and reputation of organizations handling PHI.
[1] https://www.dhcs.ca.gov/formsandpubs/laws/hipaa/Pages/1.10HIPAATitleInformation.aspx
[2] https://privacyruleandresearch.nih.gov/pr_06.asp
[3] https://www.hhs.gov/hipaa/for-professionals/privacy/guidance/business-associates/index.html
[4] https://www.hhs.gov/hipaa/for-professionals/security/index.html
[5] https://www.hhs.gov/hipaa/for-professionals/security/laws-regulations/index.html
[9] https://www.hipaajournal.com/hipaa-compliance-checklist/
[10] https://www.hhs.gov/hipaa/for-professionals/breach-notification/index.html
[11] https://www.hipaajournal.com/common-hipaa-violations/
[12]https://www.hipaaguide.net/recent-hipaa-changes/
[13] https://learn.microsoft.com/en-us/azure/compliance/offerings/offering-hipaa-us

